Cybersecurity has become even more important now with more people working from home. In a corporate office environment certain computer and network security issues are handled by the IT staff, but there are things you may want to do to protect yourself in your normal day-to-day situations.
If you have questions about security, get in touch.
Multi-Factor Authentication (MFA)
 This is one of the most effective things you can do to protect your online accounts.
This is one of the most effective things you can do to protect your online accounts.
Also known as Two-Factor Authentication (2FA) — it simply means that, in addition to a username/password combination (Factor One), we use a second means of verifying our identity to log in to a website or other service. This is usually done with a temporary code that it is sent to a mobile phone.
This second authentication step dramatically reduces the chance that your account will be compromised. Even if someone were to get your username and password, they would not be able to log in without the unique code. If you use 1Password for password management, the app can generate one-time password codes for you. I use this feature every day.
Many websites and online services now offer an MFA/2FA option, and I highly recommend enabling this everywhere it is available.
Use Strong Passwords
Simple passwords like “Password123” are easy for someone to guess, which makes your data far less secure. Strong passwords are much harder to guess and contain a mix of upper- and lowercase letters, numbers, and other characters.
Strong passwords are also harder to remember, so I recommend using a good password manager program like 1Password, LastPass, or Dashlane. I have been using 1Password for years to keep all my passwords synced between my Mac, iPhone and iPad. A password manager will securely store and remember your complex passwords for you.
Phishing
 Hacking into someone’s computer is not easy. It’s much easier to trick people into handing over their login information by pretending to be a legitimate website, preferably one you already use and trust, like your bank or email provider.
Hacking into someone’s computer is not easy. It’s much easier to trick people into handing over their login information by pretending to be a legitimate website, preferably one you already use and trust, like your bank or email provider.
It usually comes in the form of an email that appears to be from a company you use. It will have their logo and branding, and usually looks perfectly legitimate. The message typically warns that you need to log in and change your password, or “confirm” your account, or take some step to mitigate a problem. The link provided takes you to a phony website that also looks legitimate, but it is a scam created to capture your username and password so they can gain access to your account.
Any time you get an email prompting you to click a link and enter your login information, view this as a huge red flag. Your bank will not do this, nor will any legitimate company. If you think there may be a real issue with your account, call the company and find out. Or navigate to their website yourself — never click the link in the email.
Secure Websites / HTTPS
Most websites that should be doing this are already doing it — certainly your bank has it, and major e-commerce sites like Amazon — but it’s worthwhile to confirm before you enter sensitive information into any site (passwords, credit card info).
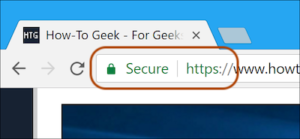
In your browser, look at the address bar where the website address is located. If there is a padlock icon and the site address begins with HTTPS, it is a secure connection. If it begins with HTTP, it is not secure.
The padlock and HTTPS means that the website has a security certificate installed which will encrypt the communications between your computer and the site. If a hacker were to intercept your connection they would not be able to see the data you have typed into the site. Look for the padlock, and if it’s not there, don’t enter any sensitive information.
VPN
 VPN stands for Virtual Private Network. It is a secure encrypted network connection. What this means is that when you send information over the internet — usernames, passwords, messages — the data is scrambled up into random characters as it travels over the network, and it is decrypted only when it reaches its destination. So if someone were to hack your network connection they would not be able to read the information traveling over the VPN. A VPN will also provide a different IP address which makes it appear that you are connecting to the internet from somewhere else.
VPN stands for Virtual Private Network. It is a secure encrypted network connection. What this means is that when you send information over the internet — usernames, passwords, messages — the data is scrambled up into random characters as it travels over the network, and it is decrypted only when it reaches its destination. So if someone were to hack your network connection they would not be able to read the information traveling over the VPN. A VPN will also provide a different IP address which makes it appear that you are connecting to the internet from somewhere else.
There are VPN apps you can install on your Mac or Windows computer, and also on your mobile phone. This is important when using a public WiFi network, like at an airport, coffee shop, library, etc — we don’t know if these networks are secure, so always assume that they are not.
When I use a public WiFi network on my Mac or iPhone, I switch on my VPN before doing anything on the internet. This way, if someone were monitoring network traffic they would not be able to see any data that is being transmitted from my device. When I’m done, I switch off the VPN.
If you are working from home your employer may provide VPN software for you to connect securely to the office.
Email Attachments
 Do not open email attachments that appear to be even slightly questionable. If you are not certain of the source, carefully check the sender’s email address or call them and ask about it.
Do not open email attachments that appear to be even slightly questionable. If you are not certain of the source, carefully check the sender’s email address or call them and ask about it.
Compromised email attachments are a common source of viruses and malware, so be alert to anything that doesn’t feel right.
Encrypted Backups
 If you use a Mac you can have Time Machine automatically encrypt your backup data. If someone were to steal your backup drive they would not be able to access your data without the encryption key (password).
If you use a Mac you can have Time Machine automatically encrypt your backup data. If someone were to steal your backup drive they would not be able to access your data without the encryption key (password).
If you do this, it’s very important to make a note of the encryption key that you choose. Without the encryption key you will lose access to your data and it will be unrecoverable.
Secure Browsing
There are several browser options for Mac and Windows. I’ll focus on the Mac here.
Safari

Apple’s browser that comes with all Macs and iOS devices is Safari. Apple has done a very good job with Safari and made it one of the better privacy-focused browsers you can get. It helps prevent websites from tracking your browsing activity, provides strong password options, and protects from harmful websites that contain malware (malicious software), among other things.
Read more about it at apple.com/safari.
Firefox

I like Mozilla’s Firefox as an alternate browser. Like Safari, it’s a privacy-focused browser with a particular feature I really like — multi-account container tabs. The benefit here is that you can have multiple tabs open in Firefox and each tab acts as its own isolated browser. Websites that are open in container tabs will not know what is open in the other tabs and cannot track your browsing activity. This is especially useful if you are on Facebook or Google — sites that make their living off tracking so they can deliver ads.
Brave
 If you like Google Chrome, consider the Brave browser instead. Brave is essentially Chrome without all the Google advertising and tracking code and it will work with your existing Chrome extensions. It also uses less of your Mac’s memory which helps with performance and battery life. I never use Chrome anymore, Brave has taken its place if I come across a Chrome-focused website or need a special extension that is only available for Chrome.
If you like Google Chrome, consider the Brave browser instead. Brave is essentially Chrome without all the Google advertising and tracking code and it will work with your existing Chrome extensions. It also uses less of your Mac’s memory which helps with performance and battery life. I never use Chrome anymore, Brave has taken its place if I come across a Chrome-focused website or need a special extension that is only available for Chrome.
